

|
|
Initiation responsibility: Head of IT Section, IT Security Management
Implementation responsibility: Head of IT Section, Administrator
IT systems in agencies and companies are typically integrated into local networks (LANs) which in turn are linked to other networks. Simply for technical reasons it is generally necessary with medium-sized and larger networks to divide a LAN into several subnetworks, for example because there is a limit on the number of IT systems per subnetwork or on the overall length of the cabling.
However, the establishment of subnetworks is also recommended for reasons of IT security. Sensitive data can be restricted to certain areas within the LAN (confidentiality), while at the same time it is possible to prevent faults in or attacks on one subnetwork from impairing the operational capability of other subnetworks (integrity and availability).
At the outset it is necessary to determine which IT systems should be operated in a common subnetwork. It is recommended here that reference is made to the results of the assessment of protection requirements and that the following procedure is adopted:
The second step entails the selection of suitable components for linking the subnetworks which have been established. Recommendations on this point will be found in safeguard S 5.13 Appropriate Use of Equipment for Network Coupling.
In particular, consideration should be given to the use of firewalls where subnetworks which contain components having a very high protection requirements are to be linked up. This will ensure that data flows to and from the subnetwork concerned in a selective and securely controlled manner.
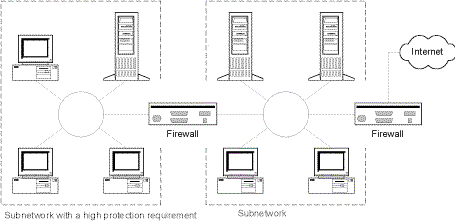
The diagram below illustrates an example of a possible overall structure for a LAN after a subnetwork having a high protection requirement has been split off from the residual subnetwork using an additional firewall. For the sake of simplification, the two firewalls are shown as single symbols, but generally they consist of several components (packet filters, application gateway etc).
Recommendations for the technical implementation of segmentation in the LAN are contained in following safeguards:
Additional controls:
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
last update: October 2000 |