

|
|
Initiation responsibility: Head of IT Section, IT Security Management
Implementation responsibility: Administrator, fax mail centre
Secure operation of a fax server requires that communication is secure both locally and also over the public switched network. The fax server accepts incoming fax transmissions from other fax servers or fax machines and if the automatic fax routing function has been activated, it then routes them to the connected users. Outgoing fax transmissions sent by the connected users are passed to the fax server and then sent on to recipients. The fax server must also ensure that local fax transmissions, i.e. fax transmissions from one workstation to another within the same organisation (or organisational unit) are sent on internally and not over the public network.
If the fax server is to be operated securely, then, once purchased and installed, the configuration of its operating system and the fax server application must be tested thoroughly. If any error messages are generated, the configuration settings should be altered where this is possible. The test phase should be followed by a pilot run. Only once the fax server has been demonstrated to be running without errors in this phase also should it be cleared for actual operation. The configuration parameters should be documented meticulously, as should all changes to the configuration settings.
Fax servers store all incoming and outgoing fax transmissions. The length of time for which these are stored depends on the facilities provided by the fax server application and the configuration. Thus, for example, it is possible that outgoing fax transmissions are only held temporarily until a given fax job has been completed and are then deleted. Again, it could be that incoming fax transmissions are only stored temporarily until they have been re-routed to recipients, following which they are deleted. However, another possibility is that all incoming and outgoing fax transmissions are held on the fax server until they are specifically deleted by the users concerned or by the fax mail centre or Administrator. On some fax servers it is also possible to have the data automatically deleted after a defined period of time. Thus, for example, all fax transmissions more than three months old are automatically deleted. Depending on the concept of use, procedures must be defined for the deletion of fax data on the fax server. At the same time, a procedure should be laid down as to where and to what extent archiving of fax data should be performed. As a general rule, fax data should not remain on the fax server any longer than is absolutely necessary.
Steps must be taken to ensure that unauthorised persons cannot access fax transmissions. As a first step, the fax server must be physically protected against unauthorised access. This can only be achieved if the server is located in a secure server room or server cabinet (see Section 4.3.2 Server room and Section 4.4 Protective cabinets).
To ensure the fault-free operation of the fax server, it is also necessary to specify who is responsible for administration of the hardware components, the operating system and the fax server application. A fax mail centre should be set up (see also S 2.180 Setting up a fax mail centre). The administration personnel and the staff employed in the fax mail centre must be given training on the operating system and fax server application. To avoid disruption due to improper use, the users must also be trained in operation of the fax client application.
Often the permissions which can be granted to users and user groups on fax servers for incoming fax transmissions include:
For outgoing fax transmissions, often the following rights can be granted:
Permissions should be granted in accordance with the provisions contained in the fax security guidelines (see also S 2.178 Creation of security guidelines for the use of the fax server).
Unless it is possible to ensure by technical means that fax transmissions are forwarded immediately, access rights should be granted in such a manner that only authorised users can access the relevant "mailboxes" on the server.
As a general rule, access to temporary areas in which the fax server application stores fax transmissions temporarily prior to their being sent out or distributed to recipients should only be granted to privileged users (e.g. administrators, fax mail centre).
The connections of the fax server to the private branch exchange or to the public switched telephone network should be checked at regular intervals to ensure that they are working properly. Where the fax server is linked to internal communications systems, such as, for example, an e-mail system or a workflow management system, the functioning of these connections should similarly be checked at regular intervals.
Regular checks must also be performed to ensure that sufficient hard disk space is available for storage of fax transmissions (see also S 5.75 Protecting against overloading the fax server). If the hard disk space becomes exhausted, no further fax transmissions can be received or sent.
The fax server activities must be logged in accordance with the provisions of the fax security guidelines and the logs must be examined at regular intervals (see also S 2.64 Checking the log files and S 5.25 Using transmission and reception logs). When specifying the extent and content of logs, the need for prompt involvement of the staff council or works council should be borne in mind.
Reservations regarding the use of a fax server are often due to the fact that an IT system which is integrated into the LAN can be accessed over the public telecommunications network.
Through careful selection and configuration of communications cards, operating system and fax server application and secure positioning of the server in the network topology, the danger of penetration of the network or the fax server can be reduced to a minimal residual risk.
Where active ISDN cards are in use, features which are not necessary for receiving and sending faxes should be disabled (see S 4.59 Deactivation of ISDN board functions which are not required).
Where dedicated fax cards are used, once again it is important to find out at the outset exactly what facilities are provided, and, if possible, to disable any unnecessary features which are not required.
The fax service should be the only service provided by the fax server. In particular, a fax server should not be used also as a data, printer, e-mail or Internet server or as a remote access computer. To reduce the probability of penetration over the telecommunications network, the operating system must be configured as "lean" as possible. This means that services and protocols which are not really necessary for operations are not installed. For example, if the Telnet service is not started up on a fax server, then it is not possible for an attack to occur from this source. When deciding which services and protocols are necessary, it should be borne in mind that dangers often arise from the combination of different services and protocols.
How the server is securely positioned in the network topology depends partly on whether any firewall is in use in the organisation and, if so, which type.
A fax server has a minimum of one interface to each of the telecommunications network and the LAN. The fax server should be placed in the network in such a way that in the event of a successful attack on the fax server it is not possible for the adversary to penetrate the entire network. On the other hand it must not be possible to attack the fax server successfully from within the network either. For example, it is conceivable that an attack could be launched by an adversary from the Internet. If such an attack succeeds, the perpetrator is then in a position to arrange for faxes to be sent out using the fax server of the attacked organisation. This not only results in telephone charges but, even more serious, could harm the company's reputation. If the attacker succeeds in getting through, he will also be able to view the fax transmissions stored either permanently or temporarily on the fax server, despite not being authorised to do so. Similarly, attacks by insiders over the LAN are also feasible.
As a fax server usually is not the only IT component which is connected to an external network, there will normally be a barrier to protect the internal network against external networks (see also Section 7.3 Firewalls).
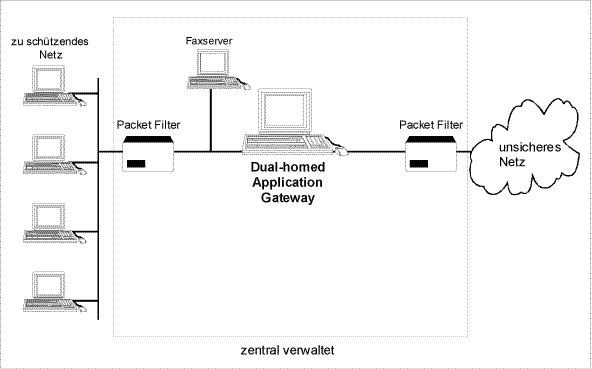
If there is a screened subnet acting as Internet firewall (configuration 1 from S 2.73 Selecting a suitable firewall), the fax server should be positioned between the inner packet filter and the Application Gateway (see Figure 1). The Application Gateway and the outer packet filter provide sufficient protection against attacks from the insecure network. The fax server is protected against attacks from the internal network by the inner packet filter.
Additional controls:
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
last update: Januar 2000 |