

|
|
Initiation responsibility: Head of IT Section, IT Security Management
Implementation responsibility: Administrators
Establishing and updating filter rules for a firewall is not a simple matter. The administrator must have an in-depth knowledge of the protocols used and be trained accordingly.
When establishing the filter rules, the following points should be observed:
The filter rules should be summarised in a table, with one axis representing the destination computer addresses, and the other axis the source computer addresses. The entries contain the permissible port numbers, the top one being the source port, the lower the destination port. Packet filters can check the packets immediately after receipt or before rerouting them. Here, filtering should be performed for the packets entering the packet filter. Furthermore, the packet filter should be configured in such a way that only the addresses of the computers connected to the interface are permitted as the sender address. Addresses connected with other interfaces are not permitted. This reduces the threat of IP spoofing attacks.
Example:
The following table contains filter rules for the internal interface of a packet filter between an internal network and a screened sub-net i.e. a sub-network located between the internal and the external network and which monitors the connections between them (see Fig. 1 in S 2.77 Secure Configuration of Other Components).
The entries contain the permissible connections, the upper entry being the source port, the lower being the destination port.
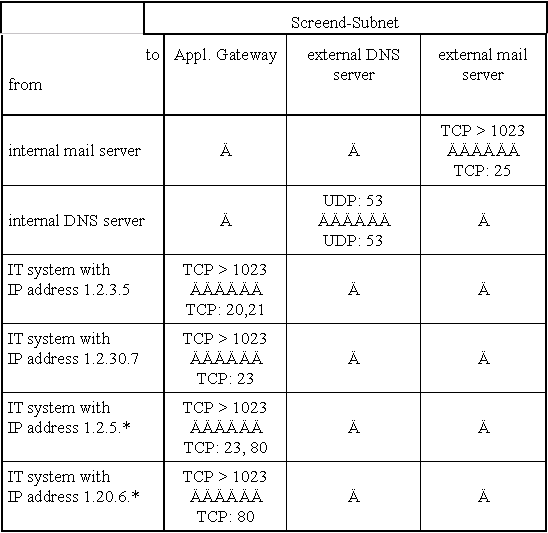
This table must then be transformed into appropriate filter rules. This is frequently not simple and must therefore be checked precisely. On the basis of regular tests, it should be ensured that all filter rules have been correctly implemented. In particular, it must be ensured that only the services set out in the security policy are permitted.
For the rules of an application gateway, similar tables must be established. These tables are to be implemented in rules.
Example:
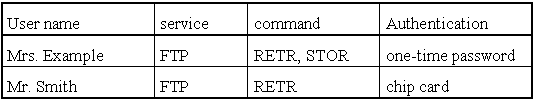
Mrs Example can use the commands RETR and STOR of the service FTP, i.e. she can load and send files via FTP, whilst Mr. Smith can only load files.
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
July 1999 |