

|
|
 |
2.4 Basic Security Check
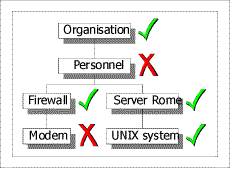
In the discussion below it is assumed that for a given set of IT assets a summary was prepared of the existing assets, their installation locations and the IT applications supported, based on the IT structure analysis of the IT assets. Building on this, the protection requirements were then assessed, resulting in an overview of the protection requirements of the IT applications, the IT systems, the rooms in which IT assets are used and the communication links. This information was then used to perform IT baseline protection modelling of the IT assets, in the course of which the IT assets under consideration were mapped to modules in the manual.
This IT baseline protection module is now used as a test plan to establish, using a target versus actual comparison, which standard security safeguards have been adequately implemented and which have not been satisfactorily implemented.
This section describes how to perform the basic security check in the context of the central task of drawing up an IT security concept which affords IT baseline protection. This basic security check consists of three different steps. The first step entails making the organisational preparations and in particular selecting the relevant contact persons for the target versus actual comparison. In step 2 the target versus actual comparison is performed using interviews and sampling checks. In the final step, the results of the target versus actual comparison are documented, together with the reasoning behind it.
These three stages of the basic security check are described in detail below.
2.4.1 Organisational Preliminary Work
To ensure that the target versus actual comparison proceeds smoothly, a certain amount of preliminary work is required. It is necessary first to inspect all the in-house documentation which controls IT security-relevant processes, e.g. organisational instructions, work instructions, security instructions, manuals and "informal" procedures. These documents can be helpful in ascertaining the degree of implementation, especially for questions about existing organisational procedures. It is further necessary to clarify who is currently responsible for their content, in order to be able subsequently to determine the correct contact person.
It must then be established whether and to what extent any external parties need to be involved in ascertaining the implementation status. For example, this might be necessary if there are any external computer centres, external parent organisations, companies to which parts of the IT operations have been outsourced or building authorities which are responsible for infrastructural measures.
Another step which needs to be performed before the target versus actual comparison can be carried out is to ascertain who are the right people to interview. Here one should start by establishing a primary point of contact for every individual module which has been used in modelling the existing IT assets.
In many cases the main point of contact will not be able to provide information on every aspect of the relevant module. In such cases it is useful to include one or more additional persons in the interview. Guidance as to which persons should be involved is provided in the entries "Initiation responsibility" and "Implementation responsibility" which are to be found at the beginning of every safeguard description.
A schedule, possibly including alternative dates, should be prepared to cover the interviews with the system administrators, administrators and other contact persons. Special attention should be given here to co-ordinating appointments with persons from other organisational units or other agencies/companies.
Depending on the size of the project team, tasks should be allocated between different teams of interviewers. Experience shows that working in two-man teams works very well. Here one person writes down the answers and comments on them while the other is asking the necessary questions.
2.4.2 Performing the Target Versus Actual Comparison
Once all the necessary preliminary work has been completed, the actual survey can begin on the previously agreed dates. This entails working through the safeguards contained in the module for which the person being interviewed is responsible in sequence.
The answers regarding implementation status for the individual safeguards may be classified into the following categories:
| "Unnecessary" | Implementation of the recommended safeguards is not necessary in the form suggested as other measures (e.g. safeguards which are not contained in the IT Baseline Protection Manual but achieve the same effect) already provide sufficient protection against the relevant threats, or else the measures recommended are not relevant (e.g. because certain services have not been implemented). |
| "Yes" | All the recommendations in the safeguard have been implemented effectively and in their entirety. |
| "Partially" | Some of the recommendations have been implemented, while others have not yet been implemented or only partially implemented. |
| "No" | Most of the recommendations contained in the safeguard have not yet been implemented. |
Reading out the text of the recommendations contained in a given safeguard during the interview is not recommended as the manual was not designed for this purpose. Hence, the interviewer needs to be familiar with the contents of the module. If necessary, handy checklists containing keywords should be prepared in advance of the interviews. In order to be able to clarify any disagreements in case of doubt, it is nevertheless useful to have the full text of the safeguards at hand. Direct entry of the answers into a PC during the interview is likewise not recommended as it would be distracting to those involved and cause unwanted interruption to communication.
If the interview begins with a few introductory words and the purpose of the basic security check is briefly introduced, this can help to create a relaxed, open and productive atmosphere. It is recommended continuing by naming and briefly explaining the safeguard. Rather than conducting a monologue, it is better to give the interviewee(s) the opportunity to go into those parts of the safeguard which have already been implemented and then discuss any items still at issue.
The questions asked should always be directed at the level of standard security safeguards, and only after the basic security check has been completed should any more far-reaching aspects of highly sensitive applications be considered. If there is a requirement to verify the statements made in the interviews, this could be achieved, for example, by examining samples of the relevant procedures and concepts, in the case of the area of infrastructure by visiting the objects under investigation on-site with the contact person, and/or by checking client and/or server settings in selected IT systems.
To conclude each safeguard, the interviewee should be informed of the assessment result (i.e. safeguard implementation status = Unnecessary/Yes/Partially/No) and this decision should be explained.
2.4.3 Documentation of Results
When it comes to documenting the results of the basic security check, some forms are provided on the CD-ROM which comes with the IT Baseline Protection Manual (see Annex: Additional Aids). The directory contains a file in Word format for every module of the IT Baseline Protection Manual, in which the results of the target versus actual comparison can be entered in tabular form for every safeguard in the given module.
First of all at the beginning of the form the following information should be entered in the fields provided:
The actual results of the target versus actual comparison are entered in the table contained on the form. For each safeguard in the relevant module, the fields should be completed as follows:
An example of a completed survey form is provided at the end of this section.
The results can also be documented using a tool, for example the IT Baseline Protection Tool which was specially developed for the BSI. This tool serves as a convenient way of analysing and auditing the results, for example, it is possible to search for particular entries, generate user-defined reports, perform various statistical analyses etc.
| Number of the IT-system | S5 | Date | 24 May 2000 | Persons interviewed | A. Müller |
| Designation: | Communications server for Intranet | Author: | N. Meyer | - " - | C. Schulz |
| Site: | Bonn, Room 3.10 | - " - | C. Schmitt | ||
| - " - | |||||
| - " - |
| Safeguard Priority | Module: Server-supported Netware | Unnecessary | Yes | Partially | No | Implementation | Person responsible | Notes / reason(s) for non-implementation | Cost estimate |
| S 1.28 (2) | Local Uninterruptible Power Supply (UPS) | X | 31/12/01 | A. Müller | There is a UPS for the server, but it has insufficient capacity. | DM 1,000 | |||
| S 1.29 (3) | Adequate Siting of an IT System (optional) | X | DM 0 | ||||||
| S 1.32 (1) | Adequate siting of the Consoles, Devices with Exchangeable Data Media, and Printers | X | DM 0 | ||||||
| S 2.03 (2) | Data Media Control | X | Necessary for IT operation | ||||||
| S 2.04 (2) | Maintenance/Repair Regulations | X | This safeguard is not being implemented as maintenance and repair is all performed in-house. | --- | |||||
| S 2.09 (2) | Ban on Using Non-Approved Software | X | 31/12/00 | N. Meyer | DM 0 1 day p.a. | ||||
| S 2.10 (3) | Survey of the Software Held | X | 30/6/00 | C. Schulz | DM 0 10 days p.a. | ||||
| S 2.13 (2) | Correct Disposal of Resources Requiring Protection | X | DM 10,000 | ||||||
| S 2.22 (2) | Escrow of Passwords | X | 31/12/00 | A. Müller | Depositing of passwords is recommended but is not consistently performed. It is hoped to introduce a systematic procedure. | DM 0 2 days p.a. | |||
| S 2.25 (1) | Documentation of the System Configuration | X | DM 0 3 days p.a. |
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
last update: October 2000 |